The primary duty in crafting a solution is to implement stringent security protocols and countermeasures. HyperTrends places a high emphasis on system robustness by weighing cost benefits, which in turn significantly affects business operations. What, then, constitutes real expertise? It’s not merely in providing a solution—that’s expected. True expertise lies in achieving excellent design at minimal expense, a principle that guides our system architectures.
With this in mind, the article delves into our specialized knowledge on security tactics tailored to specific scenarios. Security is a broad field, so I focus specifically on strategies for DDoS mitigation using AWS services, providing a valuable case study.
One instance saw one of our microservices flagging a DDoS attack. While it wasn’t critical, it prompted our client to consider the detailed insights our draft offered on DDoS strategies. I believed this could serve as a useful reference for others, too, which led to the development of this article.
Framework with the DDoS protection layers within AWS
This framework outlines the potential implications of DDoS across various stages of infrastructure. I have detailed the different options available for your system within AWS. This approach is one of the simplest ways to integrate all possible scenarios and their corresponding solutions.
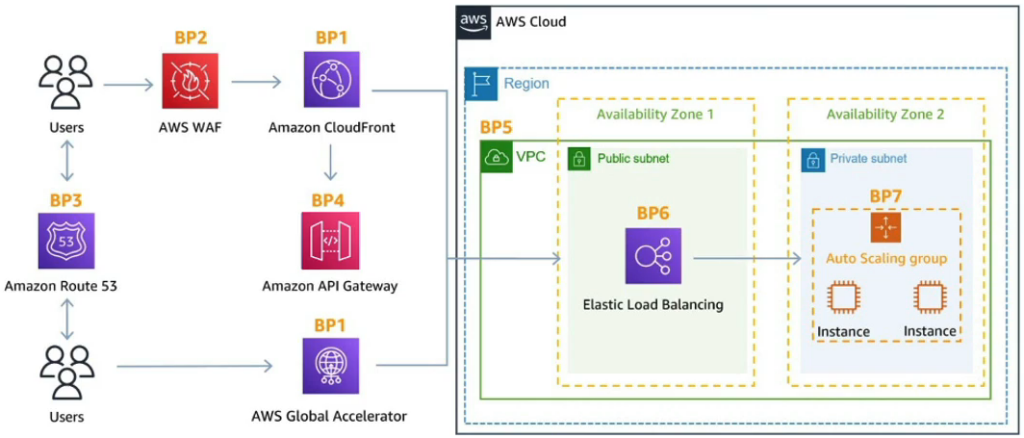
1. Edge Location Mitigation
- CloudFront (BP1): CloudFront serves as a web application delivery network that operates at the edge, inherently defending against common DDoS attacks such as SYN floods and UDP reflection. This global content delivery service accelerates the delivery of your websites and content using a worldwide network of data centers (edge locations).
- Global Accelerator (BP1): AWS Global Accelerator improves the accessibility of your applications for users worldwide. It is particularly effective when your user base is globally dispersed. Integrated with AWS Shield, it provides DDoS protection, making it a robust choice when the backend system doesn’t support CloudFront.
- Route 53 (BP3): Route 53 manages domain name resolution at the network edge, incorporating DDoS protection mechanisms. This service ensures that user requests are routed to the nearest endpoint for improved performance and availability, while also safeguarding against DNS-level attacks.
2. Infrastructure Layer Defense (BP1, BP3, BP6)
- Amazon EC2 Protection: Protecting EC2 instances from high traffic volumes is crucial. Utilizing AWS services like Global Accelerator, Route 53, CloudFront, and Elastic Load Balancing ensures that your infrastructure can handle unexpected surges in traffic, typical of DDoS attacks.
- Auto Scaling (BP7): Auto Scaling with EC2 is vital for managing sudden spikes in traffic, which can occur during DDoS attacks or flash crowds. This feature automatically adjusts the number of EC2 instances up or down according to conditions you define, ensuring that the infrastructure can adapt to traffic demands.
- Elastic Load Balancing (BP6): This service scales as traffic increases and distributes incoming traffic across multiple EC2 instances to maintain balanced load. This not only helps in handling large traffic volumes effectively but also in mitigating DDoS attack impacts by dispersing the load.
3. Application Layer Defense
- AWS WAF and CloudFront (BP1, BP2): AWS WAF, used in conjunction with CloudFront and the Application Load Balancer, helps detect and filter out malicious web requests. It allows you to write customizable web security rules to block common exploit patterns, which can prevent attackers from compromising or slowing down your application.
- Managed Rules and Rate-based Blocking: Implementing managed rules in AWS WAF provides an additional layer of security by using IP reputation lists to block requests from known malicious IPs and by setting rate-based rules that automatically block IPs engaging in abnormal request patterns.
- Geographic Blocking with CloudFront: CloudFront’s capability to block or allow traffic based on geographic location is an effective tool against region-specific threats and can be crucial in enforcing geo-based access policies.
4. Attack Surface Reduction
- Resource Obfuscation (BP1, BP4, BP6): Using services like CloudFront, API Gateway, and Elastic Load Balancing can obscure your backend resources (e.g., Lambda functions, EC2 instances) from direct public exposure, reducing the risk of attacks.
- Security Enhancements with Network ACLs and Security Groups (BP5): Network ACLs and security groups are essential for regulating traffic at the subnet and instance level, respectively. They provide a way to enforce strict traffic filters which can be crucial in preventing unauthorized access and mitigations against potential attacks.
- API Gateway (BP4): API Gateway can be configured to minimize the attack surface further. Features like burst limits, headers filtering, and the use of API keys enhance the security of your APIs by preventing abusive access patterns and providing finer control over how the APIs are accessed.
Conclusion
In conclusion, the selection of DDoS mitigation strategies within the AWS ecosystem should be guided by a balance between cost and benefit. By leveraging AWS’s robust cloud systems, businesses can deploy effective defenses against DDoS attacks that not only minimize potential downtime but also offer a cost-effective solution compared to the potentially high financial impact of successful attacks. The choice of specific AWS services—whether CloudFront, Global Accelerator, Route 53, or others—should be made with careful consideration of the particular needs and vulnerabilities of your infrastructure. Ultimately, the decision on which strategies to implement should align with your overall security posture and business objectives, ensuring that your cloud system remains resilient against threats while optimizing operational costs.
Engage with Us: We invite you to engage with us in the comments below. Share your experiences, pose questions, or discuss the intricacies of AWS DDoS mitigation strategies. Let’s collaboratively explore the best practices and innovative solutions that can enhance the security and efficiency of your AWS cloud systems.
